Nunc nunc eu massa bibendum id eu quam dui leo ante nulla cras diam lectus nibh consequat odio volutpat ut ornare tincidunt sed ut pharetra pellentesque eget in vitae ullamcorper consequat quis urna scelerisque tempus tellus rhoncus in scelerisque velit libero parturient eu mauris nisl et purus arcu cras massa volutpat fermentum aliquam purus nunc a ultrices risus lectus ornare est dolor purus lorem
Lectus ullamcorper sed sed sapien morbi vulputate laoreet velit ornare feugiat vitae eget sollicitudin lobortis placerat at placerat orci ipsum sit mauris eget enim faucibus aenean enim vestibulum porttitor diam imperdiet nulla molestie urna dictum gravida magnis dui odio dignissim ut nunc elementum tincidunt ac cursus tortor vel tortor elit in vitae
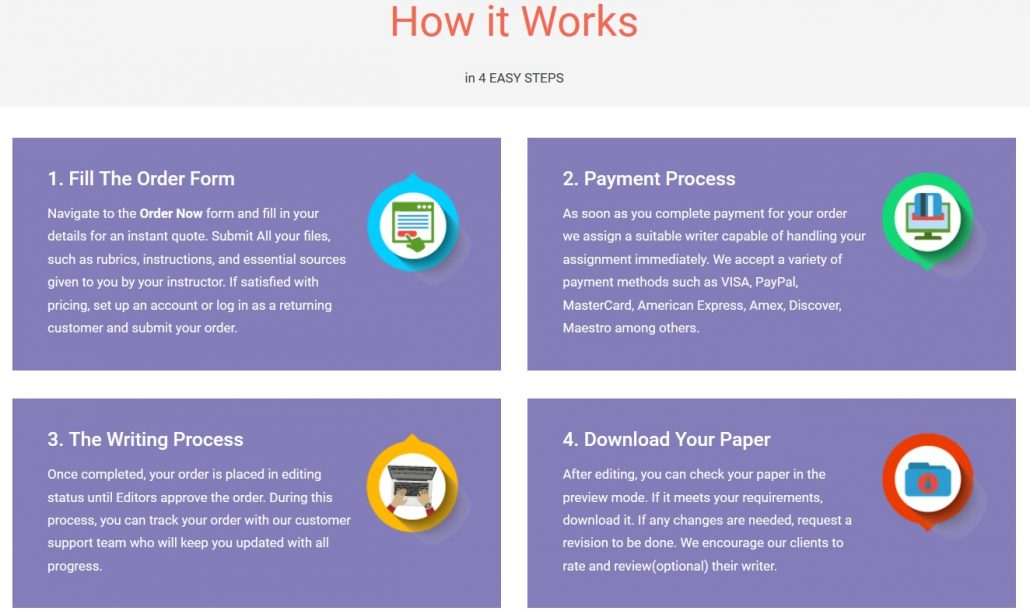
We offer assignment facilitate to students following all degrees and courses. Whether or not you’re in primary school or following a Doctor of Philosophy, we tend to square measure capable of delivering quality assignment help in the World facilitate to you.
What every nursing student needs is to find a website that offers quick help and cheap prices.
We’re sure we have the fastest writers and the cheapest prices. We offer you help of good quality for a reasonable price. This is the main reason why students keep using our website. We believe that we have completed enough orders to find out what every client needs and how we can help him or her as best we can.
Mental Health & Psychiatry
Fundamentals For Nursing
DNP Application Essay Writing
Health & Human Ecology
Human Physiology
Medical Writing Services
BSN Capstone Project
Plagiarism-Free Papers
Any Deadline, Any Subject
Confidentiality Guaranteed
24/7/365 Online Support
Qualified Nursing Writers
Direct Communication
Fair Pricing, Amazing Discounts
© Copyright 2023 Coursework Research
Hi there! Click one of our representatives below and we will get back to you as soon as possible.